
The concept of the Zero Trust security model was first coined in 2010, but global business adoption of Zero Trust has grown rapidly since the pandemic:
 |
 |
 |
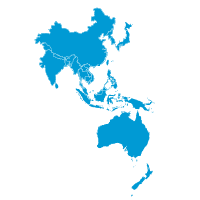
Asia Pacific (APAC)57% of businesses made Zero Trust a higher priority 20% of businesses made Zero Trust a new priority |
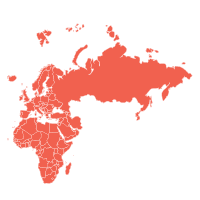
Europe/Middle East/Africa (EMEA)62% of businesses made Zero Trust a higher priority 14% of businesses made Zero Trust a new priority |
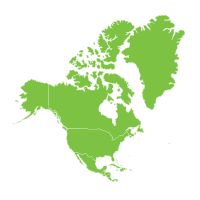
North America (NA)63% of businesses made Zero Trust a higher priority 11% of businesses made Zero Trust a new priority |
Source: Statista
Because there are several misconceptions surrounding Zero Trust, SOTI has put together a list of myths and facts to help provide clarity.
Myth 1: Zero Trust is a Product
Fact: The Zero Trust Security Model is a Strategy
You cannot go into a store or to a vendor and ask to purchase Zero Trust. Instead, Zero Trust is a business strategy of assuming everything is a threat to your data or network security.
Basically, it means that anyone or anything trying to access a network – and the sensitive data contained within that network – must state their identity through authentication and authorization. They must prove who they are before access is granted. The Zero Trust strategy is based on three pillars:
 |
 |
 |
Never Trust, Always VerifyActions and users are considered untrustworthy until proven otherwise. |
Least Amount of PrivilegeGive users the tools and access needed to complete their tasks and nothing more. |
Constantly MonitorEven after trust is granted, users, data and networks must always be monitored. |
There is no one-size-fits-all solution to Zero Trust. Organizations must examine security needs and business goals to implement the best, most effective Zero Trust security model possible.
Myth 2: Zero Trust Negatively Impacts Worker Productivity
Fact: Zero Trust Saves Time
On the surface, the idea of never trusting anything or anyone sounds like it would slow things down. However, because a large part of the Zero Trust security model works “behind the scenes”, it enables workers to stay productive while keeping data safe.
Here’s an example using device deployments: In the Zero Trust security model, the assumption is every single device poses a threat to the organization and must be constantly monitored. But having IT check the devices on a regular basis brings productivity to a standstill for both end users and IT administrators.
A technology solution which supports a Zero Trust policy can constantly monitor devices to see if they are untrustworthy. If they are, that solution can take steps to make the devices trustworthy with little, if any, disruption to the end user.
Imagine a tablet or barcode scanner that is not up to date with the latest operating system (OS) or a mobile printer not using the latest firmware. Those devices could be considered untrustworthy. A solution that automatically updates the firmware and OS makes those devices trustworthy and, in turn, keeps workers productive. It’s truly a win-win.
FOR FURTHER READING
Three Reasons to Implement SOTI Identity Multi-Factor AuthenticationMyth 3: The Zero Trust Security Model Punishes Employees
Fact: Zero Trust is About Eliminating the Concept of Trust
An organization deploying a Zero Trust security model isn’t saying its employees can’t be trusted. Rather, it is eliminating the concept of trust altogether.
One of the biggest, most impactful ways Zero Trust can help businesses and employees is by protecting them against phishing attacks. With hybrid or remote work being the norm, data access is more important than ever. As a result, 74% of remote workers have access to critical data. However, 33% of remote workers have not received any kind of cybersecurity training. Here are some of the results of that lack of training:
83% |
42% |
$4.65 million (USD) |
|
of organizations had a phishing attack in 2021. Attacks grew by six billion in 2022. |
of workers opened an unknown link or file which may have appeared trustworthy. |
is the average cost to an organization of a data breach caused by a phishing attack |
Hackers prey on our trusting nature to trick people into clicking on a sketchy link, downloading a harmful file or sharing confidential information. The Zero Trust security model takes away the choice of whether to trust a link. It assumes an email, link or file is dangerous until it has been proven otherwise
That does not equate to saying “all employees are untrustworthy.” After all, what organization would willingly hire an employee they know to be untrustworthy? Instead, it removes the inherent trust that criminals are looking to exploit.
Myth 4: Zero Trust is Only for Large Organizations
Fact: Businesses of All Sizes Can Benefit from Zero Trust
The Zero Trust security model is not exclusive to large organizations and it’s clear that small- and medium-sized businesses can benefit from it. Data breaches can have a devastating impact on smaller businesses:
- 700,000 cybersecurity attacks to small businesses in 2020 alone
- $2.8 billion (USD) in lost revenue by small businesses due to security breaches
- 40% of small businesses lost crucial data during an attack
For small businesses (or any business regardless of industry), implementing Zero Trust doesn’t have to break the budget. First, the Zero Trust security model is a mindset, not a singular product. Second, there are simple practices small businesses can utilize to achieve Zero Trust:
 |
 |
 |
Password ProtectionKeep passwords safe by using password manager, changing passwords frequently and not using 123456 (the most hacked password). |
Enable MFA50% of small businesses have not implemented MFA, which leaves valuable data and information exposed to threats. |
Have Two Plans47% of small businesses do not know how to protect themselves against an attack. Businesses should plan for attack prevention and be prepared to stop attacks in progress. |
It’s a Zero Trust World
Assuming devices and users have already been compromised and pose a threat to your business sounds alarmist, but it’s actually a smart business practice. It doesn’t mean implementing draconian measures or micromanaging employees. It’s simply a way of saying “I need to be absolutely and constantly certain that a device or person requesting access to my data or network is safe to do so.”
Adopting this mindset – and using tools to help you achieve Zero Trust – can help you save up to 43% on data breach costs. Even companies with a partial Zero Trust security model can save $660,000 (USD) per breach. If implementing Zero Trust can help you save thousands if not millions of dollars, well, it just makes sense to incorporate Zero Trust into your organization.



