Apple Enterprise Network Requirements for SOTI MobiControl
Apple services fail any connection that uses HTTPS Interception or SSL Inspection. If the HTTPS traffic traverses a web proxy, disable HTTPS Interception for the hosts listed in the Apple documentation.
You can use Apple services through a proxy if you disable packet inspection and authentication for traffic to and from the listed hosts. Attempts to perform content inspection on encrypted communications between Apple devices and services result in a dropped connection to preserve platform security and user privacy.
SOTI MobiControl needs a fully qualified domain name (FQDN) that resolves inside and outside the organization’s network. This lets the server manage devices that are locally or remotely connected. To maintain connectivity with clients, this domain name must not change. To configure your network for MDM, see Apple Platform Deployment.
You must bind a third-party commercial certificate such as GlobalSign or Let’s Encrypt to your server to verify the FQDN. Apple services do not trust internal self-signed certificates; therefore, these certificates are not suitable.
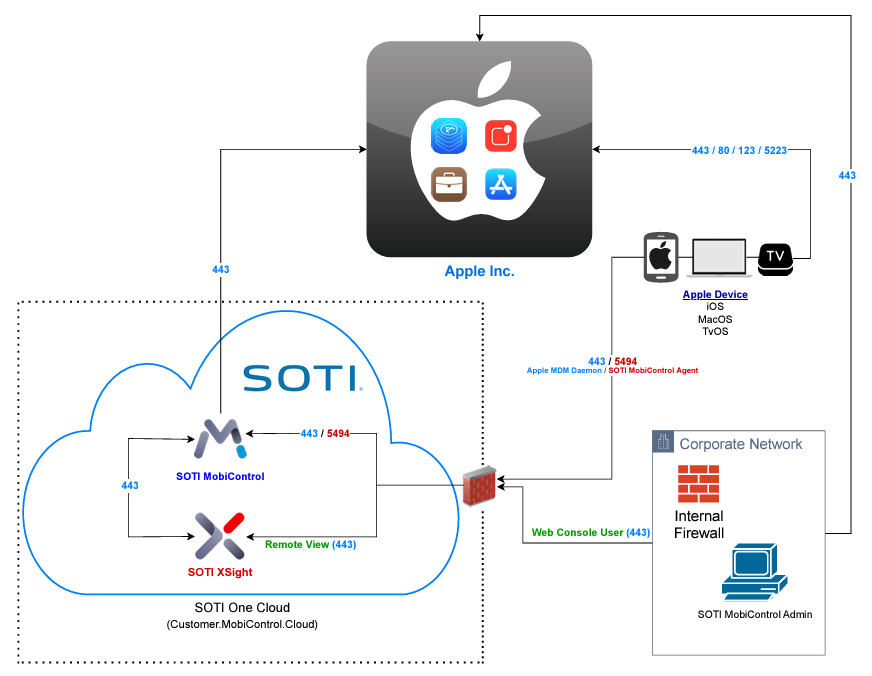
Apple Device Communication Diagram
The following diagram illustrates which firewall ports need to be open when using SOTI MobiControl to manage Apple devices.