Creating and Configuring the On-Premises Application in Azure AD
Before you begin
About this task
Configure your On-Premises application and ensure there are no conflicts with Microsoft Intune.
Procedure
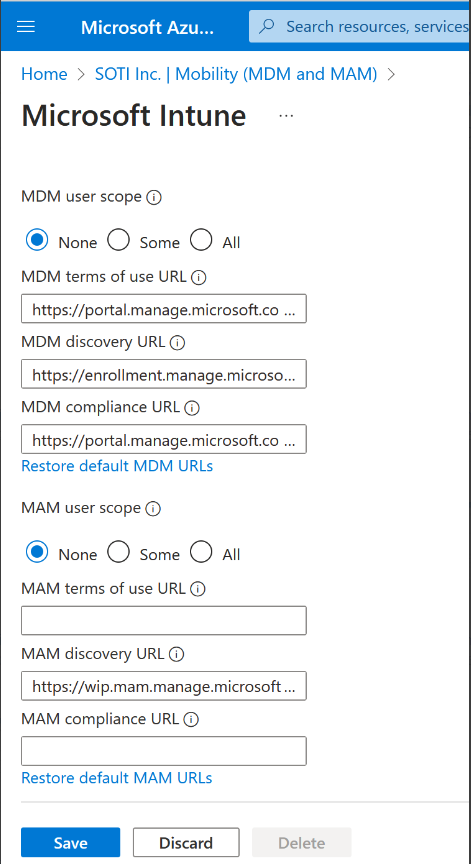
- In Microsoft Entra ID/Azure AD, navigate to Mobility (MDM and MAM).
-
Disable the Microsoft Intune app if it is present under .
Note: You must disable Microsoft Intune to prevent interference with your SOTI MobiControl On-Premises application.
- Select Add Application then Create your own application. Give your application a name then select Add.
- Set the MDM user scope to Some or All. If you select Some, you can specify which user groups to include.
-
Update the following fields with the DMA of your SOTI MobiControl instance:
- MDM terms of use URL—https://<DMA>/FederatedEnrollment/TermsOfUse.svc/TermsOfUse
- MDM discovery URL—https://<DMA>/FederatedEnrollment/Discovery.svc
Note: Find the DMA address in the SOTI MobiControl Admin Utility's Deployment Server tab.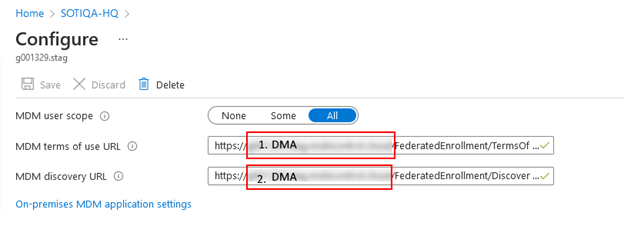
- From Azure AD, select App Registrations.
- Select the new On-Premises app.
-
Select your application.
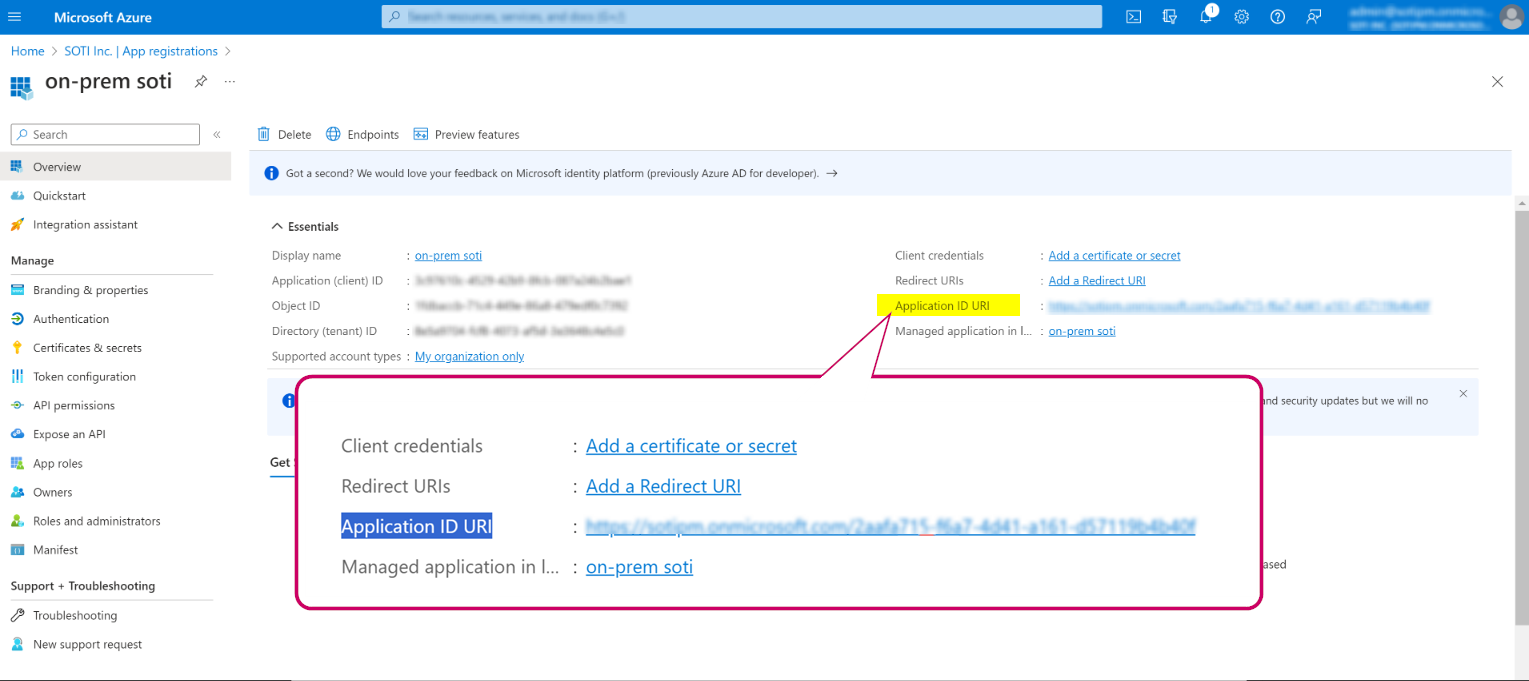
-
Select the Application ID URI and edit the value with
the DMA.
-
Select .
-
Select Application permissions and add the following
permissions:
-
Select Delegated permissions and add the following
permissions:
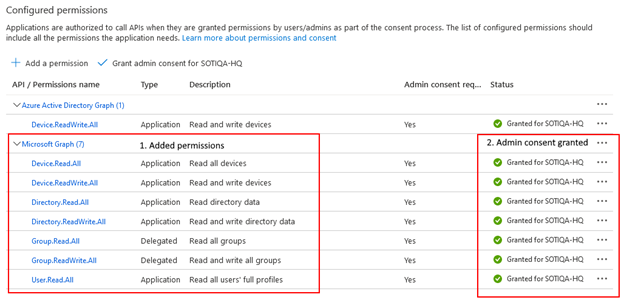
-
Select Grant admin consent for <Tenant Name>. The
status for the permissions is Granted for <Tenant
Name>.
- Select Manifest.
-
Ensure that the value for
groupMembershipClaimsis"SecurityGroup". -
Ensure that the
identifierUrisis the value you entered in the Application ID URI from the App Registration step.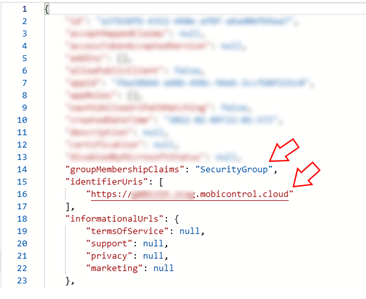 Note: If
Note: IfgroupMembershipClaimsis not"SecurityGroup", verify that the Application ID URI is correct. If set and thegroupMembershipClaimsvalue does not appear as expected, enter the following and select Save:"groupMembershipClaims": "1",Reopen the Manifest and verify
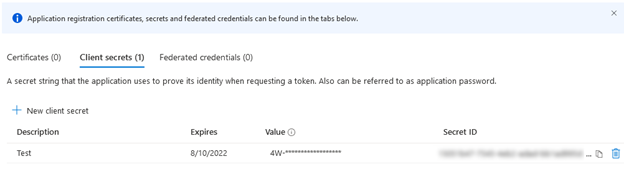
groupMembershipClaimsis"SecurityGroup", as expected. - Select Certificates and Secrets, then select New Client Secret.
- Enter a Description for the secret, set an Expiry, and select Add.
-
Copy the value and save it securely in another text file for future
reference.
Note: The value displays as masked. You cannot reread it.