Configuring Kerberos Extensible Single Sign-On (iOS/ Shared iPad User)
Before you begin
- Manage Profile permissions. See General Permissions.
- Target devices running iOS 13.0 or later.Restriction: This feature is incompatible with Shared iPads.
About this task
Procedure
- Create or edit a Reactive iOS/ Shared iPad User profile. See Creating a Profile and Editing a Profile.
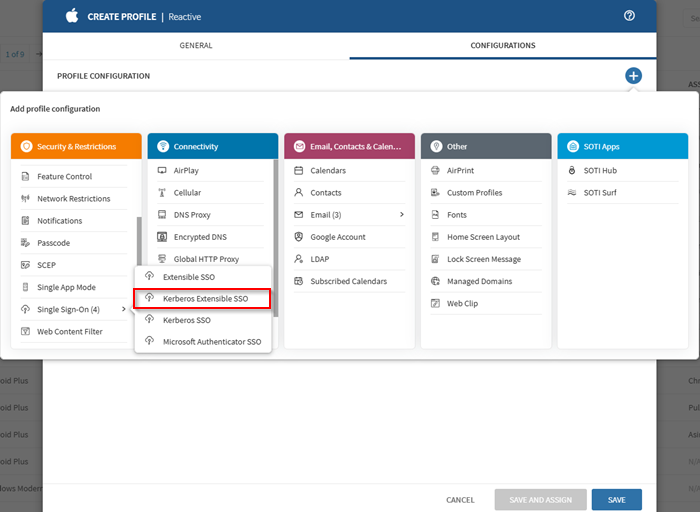
-
Add the Kerberos Extensible SSO configuration from the
Security & Restrictions configurations list.
Tip: For Shared iPad users, select Kerberos Extensible Single Sign On.
- In the Realm field, enter the IP address or hostname of the domain or administrative network partition that shares a standard security policy and authentication database.
- In the Add Host Names section, select (Add) and specify host or domain names through which the app extension can authenticate.
- Enter the Principal Name, excluding the realm.
- In the Site Code field, enter the URL of the Active Directory site used by the Kerberos extension.
- From the Certificate list, select the Public Key Cryptography for Initial Authentication (PKINIT) certificate used to renew the Kerberos credential.
-
Enable Allow Automatic Login for seamless
authentication.
Note: When disabled, passwords cannot be saved to the keychain.
- Turn on Is Default Realm if this realm should be used as the default when more than one Kerberos extension is configured.
- Enable Require User Presence to require Touch ID, Face ID, or passcode confirmation before accessing keychain items.
- Enable Use Site Auto-Discovery to allow automatic discovery of the Active Directory site using LDAP and DNS.
-
In the Add Preferred KDCs section, select (Add) to specify Key Distribution
Centers (KDCs) for handling
Kerberos traffic.
Note: The order in the list determines priority.
-
In the Add Credential Bundle ID ACL section, select (Add) to list the bundle IDs permitted
to access the Ticket Granting Ticket (TGT).
Tip: To add multiple bundle IDs, select (Import) and upload a CSV file. Each line must follow the format:
Application Bundle Identifier, Application Name. Review the list to ensure all applications are present. Missing entries may indicate a formatting issue. - Save the configuration and assign the profile to your target devices. See Assigning a Profile.