Imprivata Mobile Device Access | Single Sign On (Android)
Use the Imprivata Mobile Device Access profile to create custom connections to LDAP directories and set up Single Sign On authentication for your Android devices without using the Single Sign-On (SSO) For Shared Devices Using Imprivata MDA feature.
- Make sure for the Deployment Type, you select Mandatory.
- Enable the Manage App Config toggle and for the Enterprise Access Management server address field, add one sign server address.
Setting up the Imprivata Mobile Device Access profile
Before You Begin: To use the Imprivata Mobile Device Access profile to create custom connections to LDAP directories, you must first create an Enterprise Binding. See Enterprise Bindings for details.
- Create a profile and the Imprivata Mobile Device Access profile configuration.
- Select Manage to manage custom connections to LDAP directories.
- From the Manage Directory dialog box, select to add a connection with a LDAP directory. Then configure based on the following details:
- After configuring the LDAP directory, select Save. Then select the created LDAP directory from the Imprivata Directory.
- Later, create an app policy using the Imprivata Mobile Device Access app for devices using this profile.
| Name | The name for the LDAP connection. This name is for reference only. |
| Server Type | Select the LDAP server type. The server type determines which default search
attributes to use. Choose from:
|
| Server Address | The hostname or IP address of the LDAP server and the connection
port. The default port is 389. If using SSL, the port is 636. Note: The port can be any value that matches the
server's settings. |
| Use SSL | Turn on to make SOTI MobiControl secure the LDAP communication over a Secure Sockets Layer (SSL) tunnel. |
| Authentication Type | Choose how to connect to the server. The authentication type
should match the server's settings:
|
| Username | The username for binding to the connection when the Authentication Type is Basic or Negotiate. |
| Password | The password of the binding user. |
| Base DN (Distinguished Name) | The top level of the LDAP directory tree as the base (referred to as the "base DN"). This option defines the highest level of the LDAP search scope (also known as the RootContainer). |
| Follow Referrals | Enables searching of the binding server and the referral servers listed in the search response. |
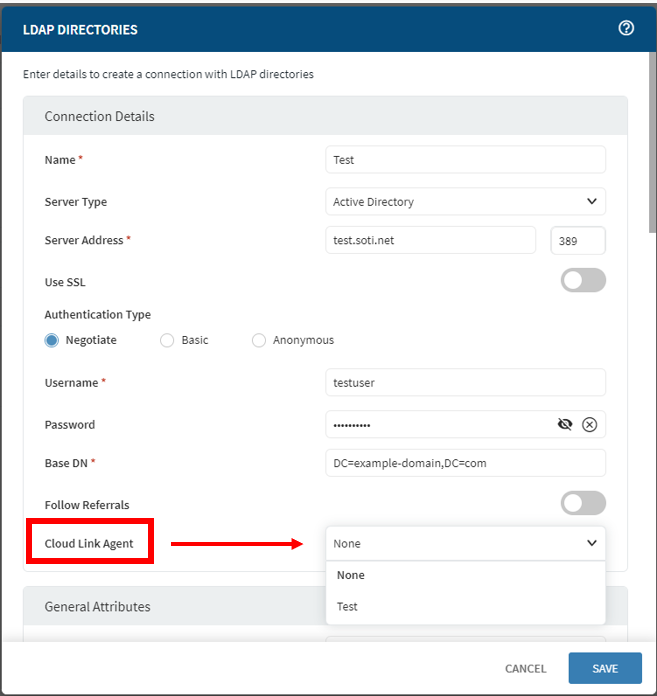
| Cloud Link Agent | This setting only applies to SOTI MobiControl Cloud
instances, not on-premises installations. Ensure you install the SOTI Cloud Link Broker CLI and set up SOTI Cloud Link Agent for SOTI MobiControl. For more information about how to setup LDAP, see Adding an On-Premises LDAP Connection. Make sure that you selected a CLA. For example, refer to the following screenshot:
|
General attributes
| Object Class | The identifier name of the Object Class, a keyword indicating this is an objectClass definition (or others). The default is "objectClass," and an alternative could be "objectCategory." |
| Object Class Group Attribute | The keyword to define the search filter for group-related searching. |
| Object Class User Attribute | The keyword to define the search filter for user-related searching. |
| Default Naming Context | The root DSE attribute for defining the root directory server entry (DSE) for the server instance. |
Group Attributes
| Identifier 1 | The keyword to define the search filter for fetching the group's object Security Identifier (SID). |
| Identifier 2 | The keyword to define the search filter for fetching the group's object Globally Unique Identifier (GUID). |
| Common Name | The keyword to define the search filter for fetching the common name. |
| Account Name | The keyword to define the search filter for fetching the account name. |
| Authentication Search Pattern | The search string for fetching the authentication information. |
| Member | The keyword to define the search filter for fetching memberships of group attributes. |
| Nested Group | The keyword to define where the search filter should look when searching groups. |
User Attributes
| Identifier 2 | The keyword to define the search filter for fetching the user's object Globally Unique Identifier (GUID). |
| Common Name | The keyword to define the search filter for fetching common names. |
| Account Name | The keyword to define the search filter for fetching account names. |
| The keyword to define the search filter for fetching user emails. | |
| Authentication Search Pattern | The search string for fetching the authentication information. |
| Add User Search Pattern | The search string for fetching the add user information. |
| SSO User Search Pattern | The search string for fetching the SSO user information. |
| User Principal Name | The keyword to define the search filter for fetching user principal names. |
| Password Last Set | The date and time that the account's password was last changed. |
| First Name | The keyword to define the search filter for fetching the user's first name. |
| Middle Name | The keyword to define the search filter for fetching the user's middle name. |
| Last Name | The keyword to define the search filter for fetching the user's last name. |
| Phone Number | The keyword to define the search filter for fetching the user's phone number. |
| Custom Attribute 1 | The keyword to define the search filter for fetching the first customized user property. |
| Custom Attribute 2 | The keyword to define the search filter for fetching the second customized user property. |
| Custom Attribute 3 | The keyword to define the search filter for fetching the third customized user property. |
| Identifier 1 | The keyword to define the search filter for fetching the user's object Security Identifier (SID). |