Single Sign-On (SSO) For Shared Devices Using Imprivata MDA
This procedure describes how to use Imprivata MDA as your app authenticator.
Before you begin
- Create an app policy with Imprivata MDA app configured. Enable the Manage app configuration toggle with one sign server address added.
- You must have a valid directory service configured in SOTI MobiControl. These credentials verify the features each user can access on the shared device.
- If a device has a Lockdown profile applied, configure Imprivata MDA as a Lockdown item. Failure to do so can result in authentication conflicts with Imprivata MDA.
About this task
To assign Imprivata MDA as an app authenticator:
Procedure
- Right-click on the group you want to apply shared devices to in the Groups tree then select Advanced Configurations.
-
Select Android Plus from the Device Type dropdown menu
then Shared Device from the list of advanced
configurations. The Shared Device panel appears.
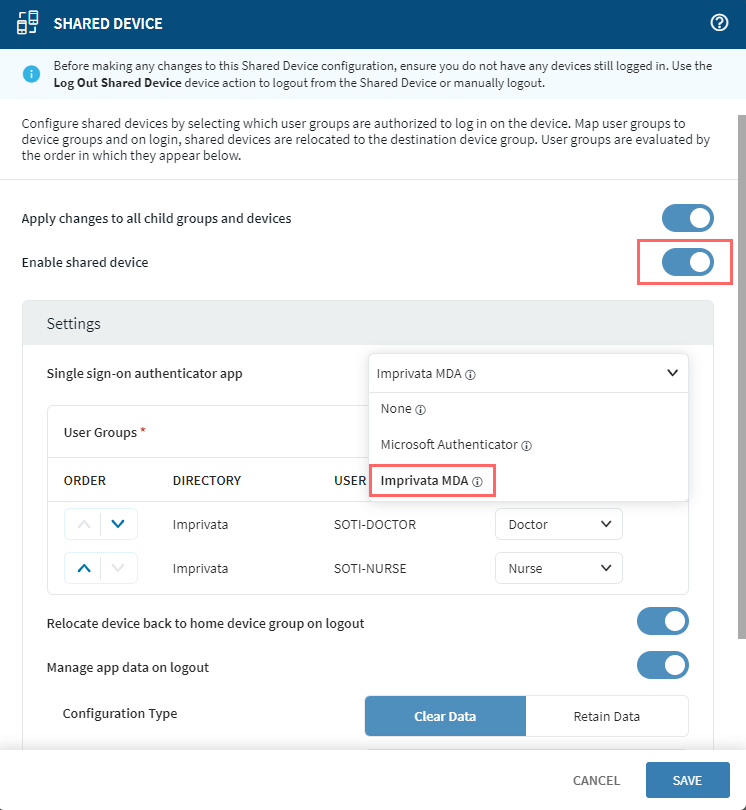
- In the Shared Device panel, select the Enable Shared Device toggle.
-
In the Single Sign-on authenticator app dropdown, choose
Imprivata MDA.
Note: The following limitations apply:
- Blacklisting Imprivata MDA with an ARC profile hides Imprivata when a user attempts to log in. The log displays Device is Pending authenticator app installation.
- Whitelisting any application (for example, YouTube, Chrome), uninstalls/hides Imprivata and the user remains logged in on the Agent. If the user tries to log out from the Agent, they get the following error: Device is Pending authenticator app installation.
- Logging into a locked NFC-enabled device with an access card does not work.
- Use passcodes on devices connected to a VPN. Only Imprivata users can log in.
- LDAP Directory Service is necessary if using Imprivata MDA as an app authenticator.