Create a Device-Based Conditional Access Policy
About this task
In Azure AD, create a device-based conditional access policy to control app access based on device compliance status.
Procedure
- Navigate to Microsoft Azure portal and select Azure AD Conditional Access.
- Select New Policy to view the New Conditional Access Policy page.
- Enter a name for the new policy.
-
Select Users and Groups then select an option such as
All Users.
Tip: Depending on licensing and permissions, Users and Groups may have alternate labels, such as Users or Users or workload identities.
-
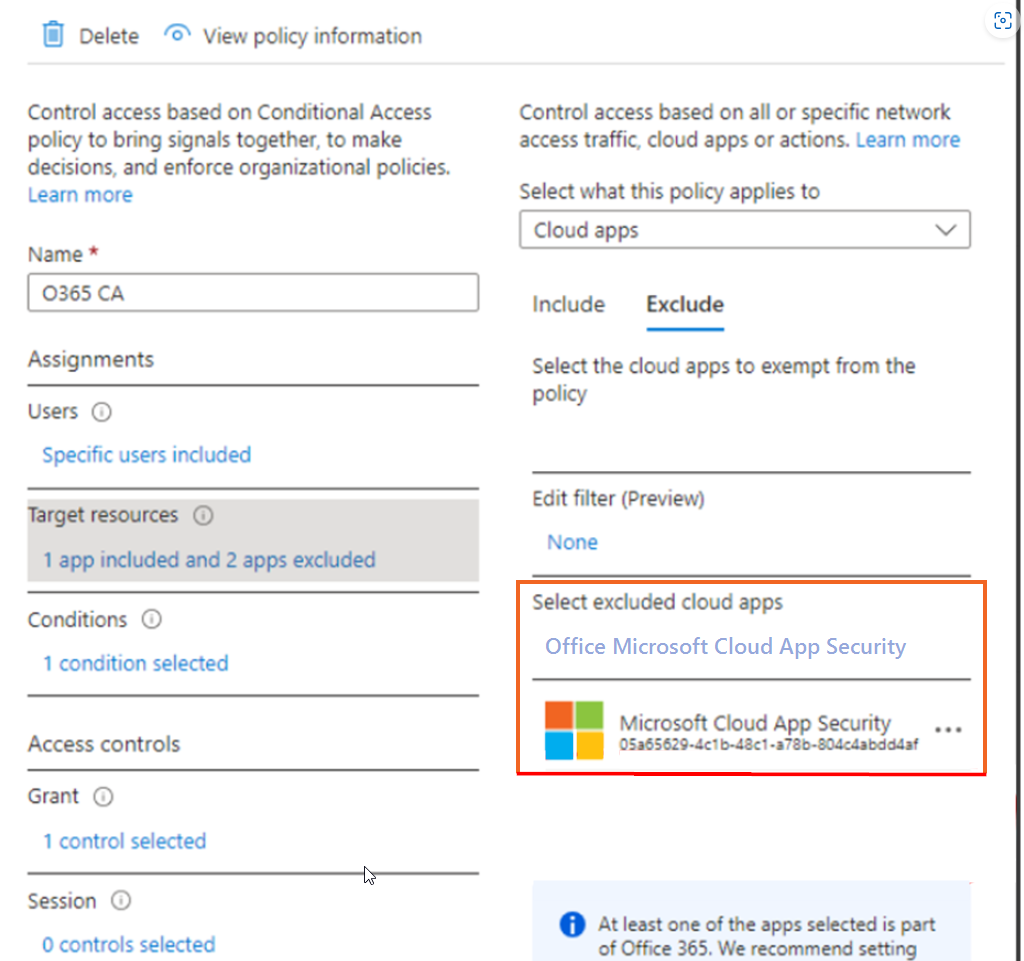
Select Cloud apps, then select the
Exclude tab.
Note:
If you choose Select Apps instead of All Cloud Apps, do not add an app related to, or named, "MobiControl" under Include. Include means that if the device becomes non-compliant, any applications included will have their access blocked. Excluded apps will not have their access blocked.
If you choose All Cloud Apps, you do not have to add anything to Include. All Cloud Apps and Select Apps should continue to exclude Microsoft Cloud App Security.
-
From Select excluded cloud apps, select Microsoft Cloud App
Security and Office 365 Exchange Online.
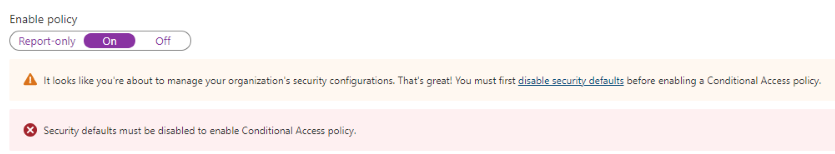
-
Select the disable security defaults link.
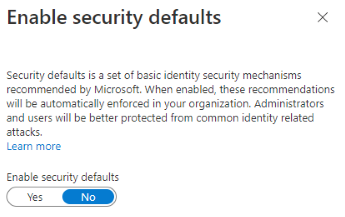
-
In the Enable security defaults panel, under
Enable security defaults, select
No. Select Save.
- Select more conditions to grant access (such as Locations).
- Under Access Controls, select Grant then Require device to be marked as compliant. Choose Select to accept.
- Under Enable policy, select On, then Create to create the conditional access policy.