Creating an iOS Enrollment Policy
Before you begin
Important: If you use a trusted third-party certificate to enroll iOS
devices, bind it to the Deployment Server Extensions and Web Console and
iOS Profile Signing components in the SOTI MobiControl
Administration Utility. Then, disable Require Trust Profile During
Enrollment.
Procedure
- From the main menu, select . The Enrollment Policies view appears.
-
Select New Enrollment Policy. The Enrollment
Policy wizard opens.
- Under the Apple icon, select iOS / iPadOS. The General view appears.
- In the General view, enter a brief, descriptive name for the enrollment policy. Include a description if needed. Then select Next.
-
In the Enrollment Type section, select an enrollment
type:
- Device: Use when you want complete control over the device.
- User: Use in Bring Your Own Device (BYOD)
environments.Restriction: User-based enrollment is only supported on devices running iOS 13.1 or later. For details, see iOS Enrollment Types.
- Optional:
If you select user-based enrollment, toggle on Enable Account-driven
enrollment to simplify user enrollment. For details, see Using Account-driven User Enrollment.
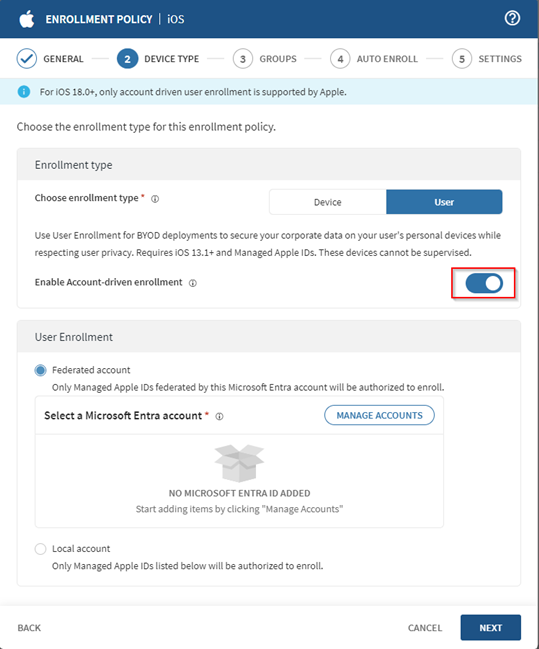
- Optional:
If you enable account-driven enrollment, select the type of Managed Apple IDs
authorized to enroll using this policy:
Federated Accounts Use a Microsoft Entra ID connection to federate your Managed Apple IDs. Local Accounts Add locally Managed Apple ID accounts. You can add up to 1,000 accounts, which must be valid email addresses (for example, user@domainoruser@domain.topleveldomain).Tip: Select Import to upload a.csvfile containing Managed Apple IDs. Include only Managed Apple IDs, one per line, with no header. -
After
choosing
your options, select Next. In the
Groups view, select if you require authentication for
enrollment. No authentication means that devices skip user verification during
enrollment. If you require authentication, select one of the following:
Option Description Password Specify a password that all devices using this policy must enter. After specifying the password, select a device group destination. Directory Select to add directory groups. Choose a directory service from the dropdown and use Search Groups to find a group. To add a new directory service, select Manage Services. From the dropdown menu, choose from: - Directory
- Identity Provider
- SOTI Identity- For more information, see Identity Management.
Tip: Users must configure OpenID Connect (OIDC) in Microsoft Entra ID to make the configured directory visible in the enrollment policy. The server URI in Microsoft Entra ID must follow this format:https://{server name}/mc/duas/oauth/2.0/azure/handleAuthCode. Replace{server name}with your SOTI MobiControl server name.After adding the directory group, select a device group destination and applicable terms and conditions.
Important: You can add more than one directory group to the enrollment policy. SOTI MobiControl assigns the authenticated device to the first directory group in the list of which the user is a member. Use the up and down arrows to arrange the list order. - Select Next. The Auto Enroll view displays.
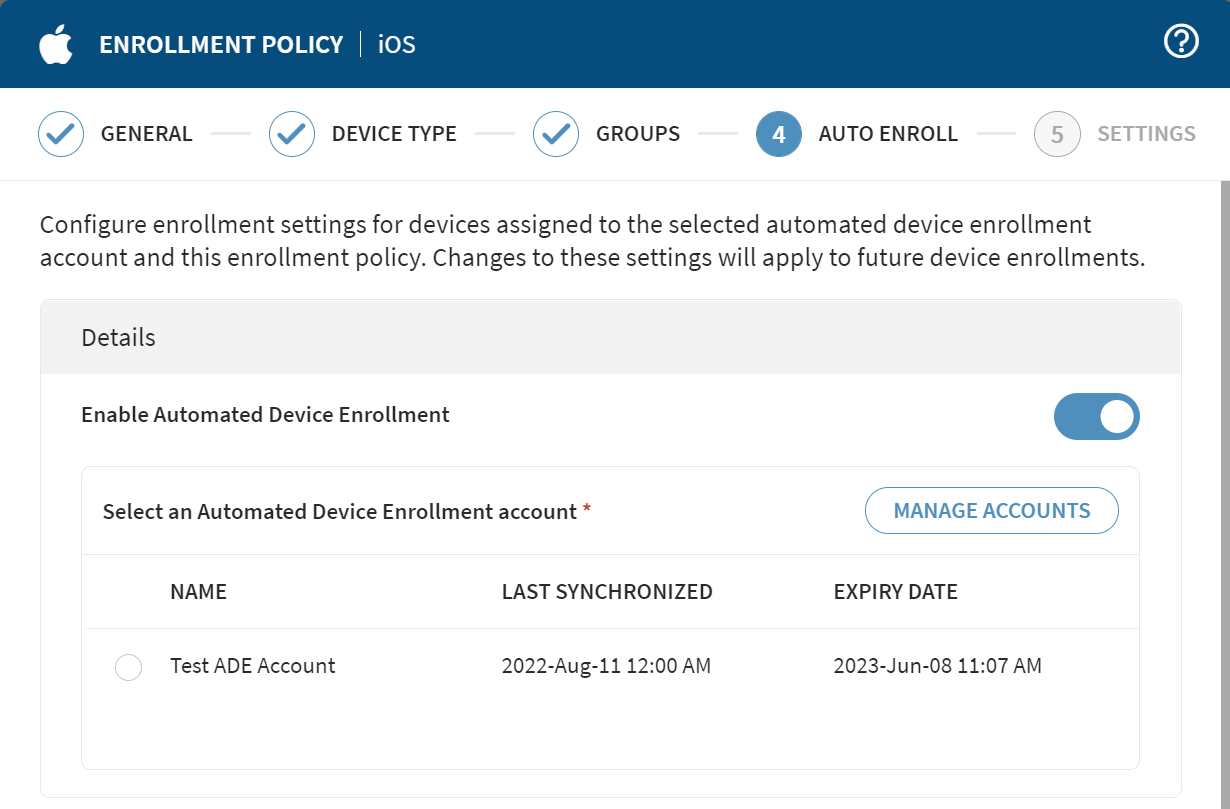
- Optional:
Select Enable Automated Device Enrollment to configure
settings for future device enrollments:
- Under Select an Automated Device Enrollment
account, choose the account you want to
use.Tip: To add a new Automated Device Enrollment account, select Manage Accounts and follow the steps in Creating ADE Accounts.
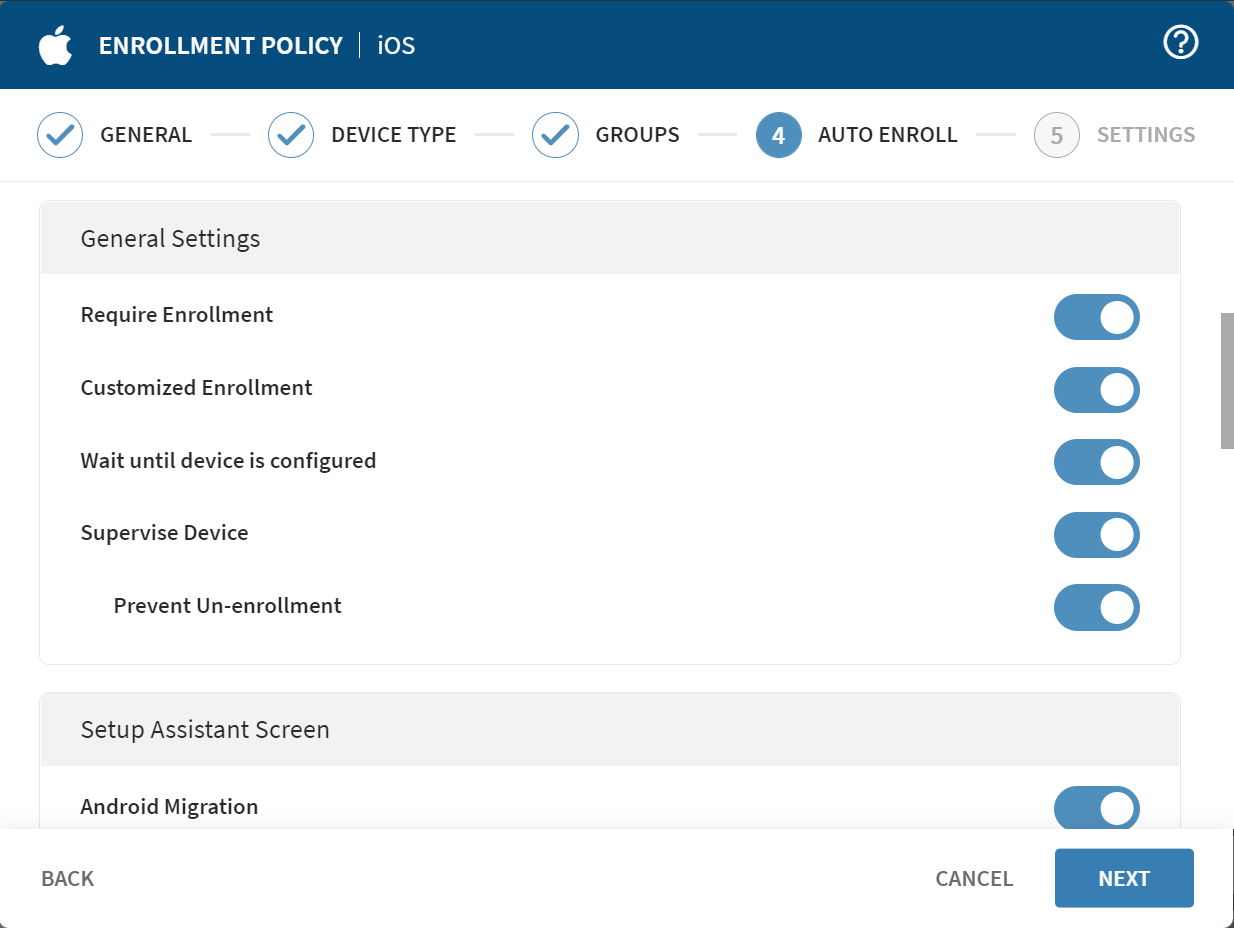
- Scroll through the available settings and select those you need.
- Under Select an Automated Device Enrollment
account, choose the account you want to
use.
- Select Next. The Settings view displays.
- Select from the available settings and then select Finish.
Results
-
 Manage Emails: Email the enrollment URL to a
recipient.
Manage Emails: Email the enrollment URL to a
recipient. - iOS Agent Enrollment ID: View and copy the enrollment ID.
- Enrollment URL: View or copy the direct enrollment URL.
- Enrollment QR Code: View or download a QR code that links to the enrollment URL.
- Download JSON: Download the .JSON registration file for the Account-driven discovery service.