Enrolling iOS Devices Using a Third Party Certificate
Before you begin
Bind a trusted third-party certificate to Deployment Server Extensions and Web Console and iOS Profile Signing in the SOTI MobiControl Administration Utility and turn off the Require Trust Profile During Enrollment setting.
Alternatively, to use the SOTI MobiControl Certificate to enroll and authenticate your devices, follow the steps detailed at Enrolling iOS Devices Using a SOTI MobiControl Certificate.
About this task
In this procedure, you'll learn how to:
Procedure
-
In the SOTI MobiControl legacy console, go to the and right-click Add Devices. Select Create Add Devices Rule to launch the Create Add Devices Rule wizard.
An add devices rule defines enrollment settings for your devices. You can create multiple add devices rules, each with different enrollment settings. However, you cannot use one add devices rule across multiple platforms.
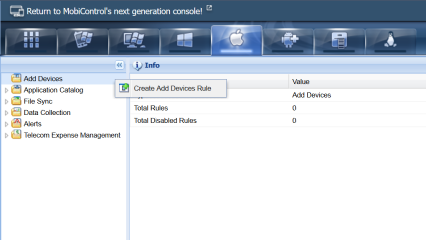
- Enter a name for the add devices rule. Make it brief, but descriptive, especially if you plan to create multiple add devices rules. Click Next.
- Enter an MDM Profile Description. This will appear to the device user.
-
Select an enrollment type:
- Device Enrollment: Use where you'll have full control over the device.
- User Enrollment: Use in BYOD environments. Only supported on devices running iOS 13.1 or later.
See iOS Enrollment Types for more information. - Optional:
For User Enrollment only: Select the type of Managed Apple IDs that will be authorized to enroll using this Add Devices rule.
Accounts Federated by Microsoft Azure AD Select to use a Microsoft Azure AD connection to authorize Managed Apple IDs. Local Accounts Select to add local Managed Apple ID accounts. You can add up to 1000 accounts. Accounts must conform to a valid email address format, such as user@domain or user@domain.topleveldomain Tip: Click Import to upload a .csv of Managed Apple IDs. The .csv should be a list of Managed Apple IDs, with no header. -
Choose the destination device groups:
Manual All devices enrolled with this rule will be placed in the same device group. On the next screen, select a device group from the list to enroll your devices into and then skip to the step for selecting a user authentication option.
Based on User Group Membership Devices will be placed into groups based on the membership of the user account assigned to the device. You'll be able to associate user groups to specific device groups later on in the wizard. Click Next.
-
Choose either LDAP Directory Service or Identity Provider and then select an identity management connection from the dropdown list. If you have not configured any connections yet, click Manage Directory Services / IdP Connections to configure a new connection in the dropdown list instead. See Identity Management for more information. Click Next.
Important: If you chose User Enrollment and Accounts Federated by Microsoft Azure AD, you must select the Identity Provider option and use an IdP connection that is backed by the same Azure AD connection you selected on the previous Managed Apple IDs screen.
-
Enter a user group (for example, administrators) that exists in your connection in the field and click Add. Once it appears under User Groups, choose a device group from the dropdown list. All members of the user group will be automatically added to the selected device group as soon as they enroll in SOTI MobiControl. If you'd like, add any terms and conditions documents. Click Next.
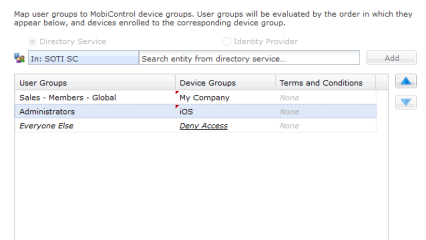
-
Select a user authentication option.
Note: These options appear only if you chose Manual for mapping your device destinations.
Utilize user groups to authenticate users during device enrollment Use a directory service or an identity provider for user authentication. Select Directory Service to select a directory service connection from the list, and search for a user group using that connection. If no directory service connection has yet been configured, select Manage Directory Services to open the Directory Service Configuration which you can use to configure a new connection.
Select Identity Provider to select an identity provider connection from the list, and search for a user group using that connection. If no identity provider connection has yet been configured, select Manage IdP Connections to open the Identity Provider Configuration which you can use to configure a new connection.
Authenticate using the Identity Provider that federates your Managed Apple IDs. Use the same Identity Provider (IdP) you selected for your Managed Apple IDs to authenticate your devices. You can allow all authenticated users to enroll with this rule or restrict enrollment by specifying which specific groups within the IdP connection can enroll. Note: This option is only available for User Enrollment add devices rules that are using Accounts Federated by Microsoft Azure AD.Password required to verify device enrollment Specify a single password for enrollment across all devices that enroll using this add devices rule. No password required to verify device enrollment Allow devices to enroll without verification. Use static enrollment challenge User static enrollment challenge. (For use with Apple Configurator.) -
Select the trusted third-party certificate from the Issue agent using dropdown list to use it as the certificate authentication authority.
If you are not enrolling devices with a third-party certificate, see Enrolling iOS Devices Using a SOTI MobiControl Certificate instead.
- Optional:
Set this add devices rule as an enrollment profile for Apple's Device Enrollment Program (DEP). Select all the options you want to apply to this enrollment profile. If you have not already configured DEP with SOTI MobiControl, click Configure DEP. Click Next.
Note: DEP is not supported on User Enrollment add devices rules.
- Optional:
Enable the Terms and Conditions setting and select a terms and conditions document from the dropdown list. If you haven't uploaded a terms and conditions document yet, click Manage to add a new document. Click Next.
Device users will be prompted to accept the terms and conditions upon enrollment.
-
Specify a naming convention for your devices. Use a combination of text and macros to automatically and intelligently name your devices.
For example, Ottawa Sales %AUTONUM% %ENROLLEDUSER_EMAIL% transforms into Ottawa Sales 001 sarah@organization.com, Ottawa Sales 002 saurabh@organization.com, and so on.
- Optional:
Choose images for your devices' lock and home screens. Click the image icon to browse your computer for image files. Toggle between iPhone and iPad to use different images on different device types.
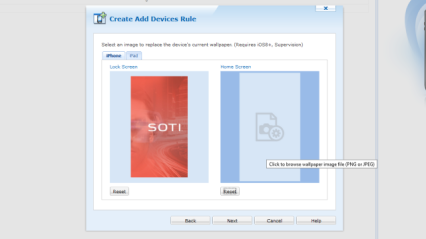 Note: You cannot specify images for user enrollment add devices rules.
Note: You cannot specify images for user enrollment add devices rules. - Review your enrollment settings. Click Back to return to a previous screen and make changes or click Advanced to adjust the rule further.
- Once you're satisfied with your enrollment settings, click Finish to save your new add devices rule.
-
Make a note of the Enrollment ID or Enrollment URL.
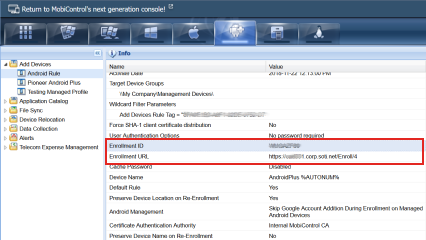
-
On your iOS device, open the Safari web browser and enter the Enrollment URL in the address bar.
If you receive a popup stating that the browser cannot verify the server identity, click Continue to ignore it and proceed to the iOS Enrollment Service web page.
- Enter the credentials you specified in the add devices rule.
- Tap Step 1 to download the SOTI MobiControl Device Enrollment Profile.
-
Tap Allow and then Install and then Install again to install the SOTI MobiControl device enrollment profile. On devices running iOS 12.2 or later, you'll need to navigate to to tap Install.
When you tap Install, you will receive a warning message with a brief description of the purpose of the SOTI MobiControl Device Enrollment Profile. Tap Trust to continue.
The installation process of the SOTI MobiControl Device Enrollment Profile includes several automatic steps that require no user interaction. Once the profile has finished installing on your device, tap Done.
- Optional: If this device is enrolled with a user enrollment add devices rule, enter your Managed Apple ID and click Enroll.
Results
You will be returned to the Safari browser where you can see if the enrollment was successful.